DevSecOps has become one of the most discussed concepts in the software development world. Many teams ask what is devsecops and why shifting security matters. The answer lies in a new way of thinking where security is not considered a bolt-on at the end of the development lifecycle, but a key part of the development lifecycle. This paper will discuss the meaning of DevSecOps, the differences between it and DevOps, its principles, the implementation of DevSecOps throughout the software pipeline, the advantages and difficulties of implementation, current tools, and recommendations on how an organization can begin implementing DevSecops.

What Is DevSecOps?
Definition of DevSecOps
DevSecOps stands for development, security and operations. It is the practice of integrating security checks, testing and governance into every phase of the DevOps lifecycle. Instead of treating security as an isolated function, DevSecOps makes security a shared responsibility among developers, operations teams and security professionals. Surveys show that DevOps teams are already embracing security practices; more than half of development teams run static application security testing (SAST), 44 % run dynamic testing (DAST) and roughly half scan containers and dependencies. By weaving security into the workflow, teams can detect vulnerabilities earlier, reduce risks and still deliver features quickly.
What Does DevSecOps Stand For?
DevSecOps literally means bringing Development, Security and Operations together. Each term carries weight:
- Development refers to the people writing code, designing features and fixing bugs. They introduce security controls and secure coding practices from day one.
- Security covers proactive testing, threat modeling, compliance, vulnerability management and policy enforcement. Security specialists provide guidance and build automation into the pipeline.
- Operations ensures that applications run reliably in production by managing infrastructure, deployment processes, monitoring and incident response. Operational teams enforce runtime security policies and maintain observability.
DevSecOps aligns these functions so that everyone has ownership over security outcomes. In a survey of 250 large enterprises, 75 % said they had already implemented DevSecOps practices and 73 % reported following a “security‑by‑design” approach where cybersecurity and regulatory requirements are addressed proactively.
The Shift‑Left Security Mindset
Traditional development does not include security testing until the end of the project. This delay means vulnerabilities that are found during deployment are costly and time consuming to correct. Studies on the Rule of Ten prove that the cost of fixing a defect increases by an order of magnitude for each stage of the software lifecycle. For example, research summarized by Code Intelligence notes that if it costs to fix a defect during unit testing, the same issue can cost to fix during system testing, costs at acceptance testing and costs after release by 10000 and 100,000 dollars, respectively. DevSecOps addresses this by security left shifting, making the testing and compliance cheaper earlier in the process, and less likely to make it to production.
Shifting left also reduces breaches. In 2024, 68 % of breaches in cloud‑native environments were attributed to oversights that could have been prevented earlier in the software lifecycle. Cost analysis supports this proactive approach; the average cost of a data breach reached US $4.88 million in 2024. The same year, Ponemon research (cited in a 2025 DevSecOps article) estimated that fixing a bug in design costs about US $80, whereas fixing it after deployment costs US $7,600, showing a nearly 100 × cost difference.
What’s the Difference Between DevSecOps and DevOps?
DevOps is more about bringing together the development and operations to deliver faster software. Test automation, deployment automation and build automation lessen friction and decrease release cycles. However, during the early DevOps practices, security was often seen as a gate to the outside. DevSecOps is an extension of DevOps that involves a concept of shifting security from the end of the pipeline to the pipeline. Key differences include:
| Aspect | DevOps | DevSecOps |
| Primary goal | Faster delivery and operational efficiency | Secure and rapid delivery with built‑in security |
| Security integration | Often handled outside the core workflow | Embedded in every phase (code, build, test, deploy, monitor) |
| Responsibility | Developers and operations take ownership for performance and reliability | Development, security and operations share accountability for security and compliance |
| Tooling focus | CI/CD automation, infrastructure provisioning | Adds security tools (SAST, DAST, SCA, IaC scanning, policy enforcement, threat monitoring) |
DevSecOps is not a way to slow down innovation. Indeed, a survey conducted in 2021 listed the following reasons as the primary motivations behind adopting DevSecOps: improving security (54 percent), quality and resilience (30 percent) and accelerating time-to-market (30 percent). While there is some concern about security being a bottleneck to increasing releases, nearly three out of four teams surveyed reported that security processes are currently a bottleneck. Pipeline security automation enables the team to become quicker and more assured.
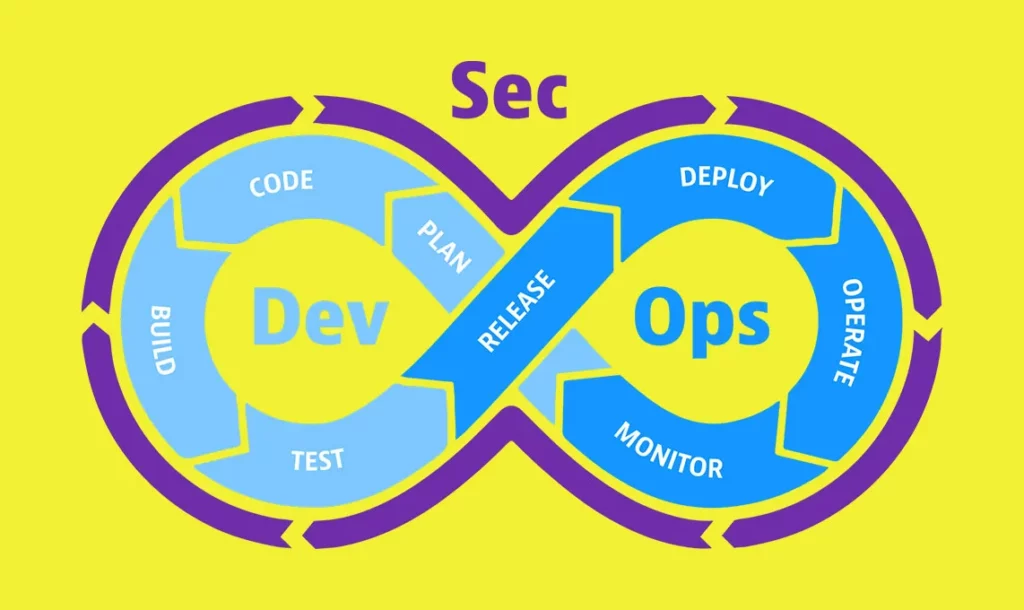
Core Principles of DevSecOps
Collaboration and Shared Responsibility
A DevSecOps culture fosters cooperative efforts across the development, security and operations. Responsibility of secure code, infrastructure and processes is shared by everyone including software engineers and system administrators.
Surveys show that organizations that follow DevSecOps often focus on security – by – design. In the Security Compass survey of large enterprises, 73 percent said they take a “by design” approach. Such a culture promotes cross-functional communication, knowledge sharing and shared accountability, de-silos.
The sprawl of toolchains may become an impediment to teamwork. According to the 2024 global survey on the topic of DevSecOps, conducted by GitLab, 74% of organizations that use AI wish to simplify their toolchains. Nearly half of DevSecOps teams use more than 5 security tools and lose around seven hours a week to inefficient processes. Consolidating tools and promoting transparency is beneficial in helping teams work together well.
Automation and Continuous Security
DevSecOps is based on automation that enables scaling the security without slowing down the development process. Manual processes become bottlenecks; 73 percent of respondents indicate that manual security and compliance testing slows the release of code. Up to 96 per cent think their organization would benefit from automating these processes. SAST, DAST, software composition analysis (SCA) and infrastructure-as-code (IaC) scanning Automated security testing (SAST, DAST) operates continuously in CI/CD pipelines such that vulnerabilities are identified early and repaired rapidly.
Automation also allows for constant compliance. Modern pipelines can automatically gather the evidence for standards such as SOC 2, HIPAA or GDPR. The 2025 DevSecOps roadmap implies staged timelines: within the first 30 days, SAST and dependency scanning will be integrated; dynamic testing, IaC scanning and secrets management will be introduced in the next 30; and runtime protection, SIEM integration and automated compliance reporting will be introduced thereafter. Such progressive automation helps the teams to build confidence without overwhelming them.
Integration and Transparency
The best DevSecOps is one that integrates security tools in the development processes and offers visibility throughout the pipeline. The tools such as GitLab, Jenkins and Azure DevOps have the capability of coordinating a build and tests and initiating security scans. As an illustration, 34 percent of organizations nowadays employ dynamic application security testing (DAST) as per a 2024 survey by GitLab, though the rate is increasing as more teams integrate DAST into pipelines. The use of continuous observability, in the form of logging, monitoring and real-time reporting assists the team in identifying anomalies promptly. The threat intelligence and AI/ML analytics also improve visibility through event correlation and predicting the possible attacks.
The Transparency is extended to supply chain security. GitLab survey revealed that 67 percent of the developers use open-source libraries, but only one out of every five organizations has a software bill of materials (SBOM). DevSecOps promotes the documentation of dependencies and the ensuring the scanning of third party components for vulnerability and license risks.
How DevSecOps Works
Code Stage
The DevSecOps pipeline begins when developers write code. At this stage, security practices include:
- Static application security testing (SAST): SAST tools scrutinize source code in search of vulnerabilities including buffer overflow, injection vulnerabilities or unprotected API usage. More than half of the DevOps surveyed teams run SAST scans. Tools such as SonarQube offer multi-language static analysis, real-time secrets detection and report that is in accordance with OWASP Top 10 and CWE Top 25.
- Dependency scanning and software composition analysis (SCA): More recent applications are highly dependent on open source packages. SCA tools are used to identify known vulnerabilities in third-party libraries. Snyk’s platform provides container images and its dependencies for integrated vulnerability detection, unified scanning and context-aware prioritization. This helps the teams to focus on the most critical issues.
- Secure coding practices: Developers receive training on secure coding guidelines (e.g., OWASP Top 10) and review code via peer review or pair programming. Enforcing these practices reduces injection flaws and misconfigurations.
Build and Test Stage
During the build and test stage, DevSecOps adds dynamic testing and container security to traditional CI processes:
- Dynamic application security testing (DAST): There are tools that perform active and passive scanning of running applications, e.g., Zed Attack Proxy (ZAP). ZAP identifies and removes vulnerabilities such as SQL injection and cross-scripting and it uses CI/CD to perform automated scans and generate detailed reports.
- Container security: Containerization is everywhere, and it is necessary to scan container images and Kubernetes workloads. Snyk offers automatic remedial and monitoring of containers. Aqua Security provides visibility of multi-clouds, real-time threat control and integration of CI/CD.
- Infrastructure‑as‑code validation: IaC templates (e.g., Terraform, CloudFormation) are to be scanned against misconfigurations and deployed. Tools such as Checkov or the scanning tools in Checkmarx One help to validate policies and to ensure insecure infrastructure is not deployed.
- Unit, integration and system testing: Tests for quality are performed regularly in addition to security tests. Automated test suites help to ensure that the program is functionally correct without causing regression.
Deploy Stage
Security should not end when code is built. During deployment, teams enforce policies and gate releases based on security criteria:
- Policy enforcement: Kubernetes policy controllers (admission controllers) or Open Policy Agent (OPA) can ensure that insecure images or configuration are not run. Checkmarx One provides application security posture management (ASPM) which tracks misconfigurations and supply-chain risks within applications.
- Secure configuration management: Credential storage is managed by secrets management tools (e.g., HashiCorp Vault). Infrastructure code is deployed only in the approved pipelines, thus ensuring that environment configurations comply with requirements.
- Controlled rollout: Techniques such as canary releases and feature flags limit the blast radius of new features. Automated rollback policies respond to failed security checks or performance regressions.
Monitor Stage
Once the application is live, continuous monitoring detects anomalies and supports incident response:
- Log aggregation and analysis: Centralized logging will receive the application, infrastructure and security tool events. SIEM/SOAR systems (e.g., Splunk, Azure Sentinel) help teams to correlate events and risk threats. This stage makes the most use of AI/ML to detect patterns and suspicious behaviour.
- Continuous vulnerability monitoring: Vulnerability scanning tools, such as Snyk, scan images of vulnerabilities that have been disclosed after deployment and alert the team on Slack or Jira. Real time threat prevention by platforms such as Aqua Security helps in blocking zero day attacks.
- Compliance and audit reporting: Pipelines are automated to gather evidence that meets regulatory standards. For example, dynamic compliance reporting can reduce the time required for audit preparation by 50 percent.
Benefits of DevSecOps
Implementing DevSecOps offers tangible benefits that extend beyond security:
- Reduced risk and fewer breaches: DevSecOps lowers the volumes of critical vulnerabilities to production by testing early and often. A shift left approach can reduce critical vulnerabilities by 60 percent. Continuous monitoring and threat intelligence thwart attackers from exploiting zero- day vulnerabilities.
- Faster release cycles and agility: Automated security eliminates human bottlenecks. In one survey, 66 percent of organizations were releasing software twice or more speedily than in the previous year. A SaaS healthcare provider case study found that the frequency of deployment improved by 40 percent following the adoption of DevSecOps.
- Better compliance and audit readiness: Continuous security testing and automated evidence collection ensures that applications meet standards like SOC 2, HIPAA or GDPR. Automated compliance leads to less manual audits and associated costs.
- Improved developer experience: Teams can be more productive when security tools can deliver feedback to the developer in a way that is easy to act upon rather than drowning the developers in noise. Some sample measures of a DevSecOps program indicated a 12 percent improvement in developer satisfaction and a 20 percent improvement in satisfaction when security was made to be invisible guardrails. Utilization of AI and automation to manage routine checks also frees developers up to do innovation.
- Financial savings: The financial impact of breaches is significant; according to IBM’s Cost of a Data Breach Report 2022 the global average cost for a data breach is US $4.88 million. DevSecOps can prevent costs associated with breaches. For example, the healthcare provider case study saved US $1.7 million every year after adopting DevSecOps.

Common Challenges in DevSecOps Adoption
Despite its benefits, DevSecOps adoption comes with obstacles:
- Technical complexity: Respondents name technical challenges as their #1 barrier. In one such survey 60 % of the respondents said that DevSecOps is technically challenging. Integrating different security tools and automating security tests demands expertise in development and cybersecurity.
- Cost and resource constraints: Approximately 40 percent of the respondents had mentioned that DevSecOps is costly. An initial investment into tooling and training is required. Half of organizations do not have enough time to implement DevSecOps and many have budget issues.
- Skills gap: Lack of education and skills was cited by 38 per cent and 36 per cent of the respondents respectively. IBM’s 2024 breach report also notes that there are serious staffing shortages with over half the breached organizations experiencing security talent shortages. Upskilling of the developers and hiring security specialists are critical.
- Organizational inertia and siloed culture: 35 per cent mentioned organizational inertia as a hindrance. Resistance to change, conflicting priorities and siloed teams can get in the way of teamwork. It is important to foster the culture of shared responsibility.
- Toolchain sprawl and inefficiency: Nearly three‑quarters of AI users want to consolidate toolchains, and 49 % of teams use more than five security tools. This proliferation leads to context switching and increases time spent managing tools instead of building features.
- Risk perception of new technologies: As AI becomes more prevalent, 55 % of respondents view its introduction into the development lifecycle as risky. Balancing innovation with privacy and data protection concerns requires careful planning.
Popular DevSecOps Tools
DevSecOps relies on a diverse set of tools to automate security and integrate it into the workflow. Below are examples of widely adopted tools and what they offer. Including these examples helps answer what is DevSecOps tools and how they support secure development.
Snyk (SCA and Container Security)
Snyk is a developer‑first platform for scanning container images, base images and open‑source dependencies. It identifies vulnerabilities in source code and containers, provides automated remediation suggestions and monitors deployed workloads for newly disclosed vulnerabilities. Snyk prioritizes vulnerabilities based on exploitability and integrates with popular IDEs and CI/CD tools. Continuous monitoring sends alerts via Slack, Jira or email, ensuring up‑to‑date protection.
Zed Attack Proxy (ZAP) – DAST
ZAP is an open‑source dynamic application security testing tool that scans running web applications for vulnerabilities such as SQL injection and cross‑site scripting. It supports automated scans during CI/CD, offers both active and passive scanning, acts as a proxy for manual exploration and generates comprehensive reports. ZAP’s extensible architecture allows custom scripts and plugins to tailor tests.
SonarQube – Static Code Analysis
SonarQube performs static analysis on code in more than 30 languages. It detects hidden vulnerabilities, secrets and code smells, supports compliance standards like OWASP Top 10, and provides real‑time feedback to developers. The tool integrates with CI pipelines and helps enforce secure coding standards early in the development process.
Checkmarx One – Code‑to‑Cloud Security Platform
Checkmarx One is a cloud‑native application security platform that combines SAST, SCA, API security and DAST into one suite. It integrates directly into development pipelines, providing real‑time feedback without disrupting workflows. The platform offers AI‑powered prioritization, application security posture management and supply‑chain security features such as SBOM generation.
Aqua Security – Cloud and Container Security
Aqua Security secures applications across their entire lifecycle in cloud, container and serverless environments. It provides visibility into multi‑cloud deployments, identifies misconfigurations and vulnerabilities, offers real‑time threat prevention and integrates into CI/CD pipelines. Aqua’s runtime protection defends against zero‑day attacks and monitors container and serverless workloads in production.
These tools are just a sample of the evolving DevSecOps ecosystem. Other notable categories include secrets management (HashiCorp Vault), infrastructure‑as‑code scanning (Checkov), API security testing (Pynt), and AI‑assisted code reviews (GitHub Copilot). Choosing the right mix depends on the organization’s architecture and risk profile.

Best Practices for Implementing DevSecOps
Adopting DevSecOps is a journey. Following structured best practices can help organizations transition smoothly:
- Start small and iterate: Rather than an all‑at‑once transformation, adopt DevSecOps gradually. The 90‑day roadmap from JSOC’s 2025 guide suggests adding static code analysis, dependency scanning and container image standardization in the first month; introducing dynamic testing, IaC scanning and secrets management in the second; and enabling runtime protection, log integration and automated compliance reporting in the third.
- Automate security in the pipeline: Integrate SAST, DAST, SCA, container scanning, IaC validation, secrets management and policy enforcement into CI/CD pipelines. Automation reduces manual effort and catches vulnerabilities before deployment. For example, 96 % of survey respondents expect their organizations to benefit from automating security processes.
- Enforce policy and access controls: Use policy‑as‑code frameworks (OPA, Kubernetes admission controllers) to automatically enforce security gates during deployment. Manage secrets securely with dedicated vaults. Define role‑based access controls and least‑privilege policies across infrastructure.
- Consolidate and integrate tools: Avoid toolchain sprawl by choosing platforms that cover multiple functions. GitLab’s survey shows that teams using AI tools want to consolidate their toolchains. A unified platform reduces context switching and maintenance overhead.
- Monitor continuously: Implement centralized logging and SIEM/SOAR solutions to detect anomalies and respond quickly. Use AI/ML analytics to reduce alert fatigue and prioritize true threats. Monitor runtime environments for newly discovered vulnerabilities.
- Document dependencies and maintain SBOMs: Track third‑party libraries and create software bills of materials. Only one in five organizations currently does this, yet SBOMs are becoming essential for supply‑chain security and compliance.
- Engage leadership and stakeholders: Securing executive buy‑in ensures sufficient resources and alignment with business goals. Highlight the financial impact of breaches (average cost US $4.88 million) and the ROI of DevSecOps initiatives (for example, $1.7 million annual savings in a healthcare case study) to justify investment.
Conclusion
Understanding what is DevSecOps is critical for organizations seeking to build secure, resilient and compliant software at high velocity. DevSecOps extends DevOps by embedding security into every stage of the development lifecycle. It emphasizes collaboration, automation, integration and continuous monitoring. Statistics show rapid market growth—with the global DevSecOps market valued at US $8.84 billion in 2024 and projected to reach US $20.24 billion by 2030—indicating widespread adoption. Businesses adopt DevSecOps to improve security and quality, accelerate time‑to‑market and meet growing regulatory demands.
At Designveloper, we have seen this transformation firsthand. Over the past 11+ years, we’ve helped global partners integrate secure-by-design practices into their systems—whether through custom software development, DevOps consulting, cloud-native modernization, or security-focused SaaS platforms.
Our team has delivered more than 200+ projects, including complex ecosystems like LuminPDF (over 60 million users) and enterprise platforms in finance, healthcare, and logistics. These projects required us to apply automation, CI/CD, threat monitoring, and infrastructure-as-code—all aligned with DevSecOps principles. That experience allows us to design reliable workflows, reduce vulnerabilities early, and ensure long-term maintainability for our clients.






Read more topics
You may also like