Zero-trust security has emerged from theory to practice. Global enterprises are losing the idea that a network perimeter can keep threats out. Reports in 2025 show that adoption is accelerating with the market for zero trust solutions worth more than USD 38 billion and forecasted to reach USD 86.57 billion by 2030. A survey of more than 2,200 IT and business leaders in 2025 found that 46 percent of large enterprises were in the process of moving to zero trust and 43 percent had already moved to zero trust (11 percent had no plans). Those who implemented the model said that it addressed half of their environment and mitigated a quarter of enterprise risk.
This article answers what Zero Trust is and delves into the architecture, core principles and use cases. It uses simple language, draws on up to date research and includes links to research-based credible reports. It also follows guidelines set by Yoast SEO in that it makes sure that the focus keyword occurs naturally throughout the content.

What is Zero Trust?
Zero-trust security is a security model that assumes that no user, device or application can be implicitly trusted. The National Institute of Standards and Technology (NIST) points out that the main idea of zero trust is to shift security away from a static network perimeter and instead focus on protecting resources such as data, services and assets. Under this model every request has to go through authentication and authorization before access. Trust is never given based on network location and/or device ownership, verification relies on user identity, device posture and context.
Major technology vendors express the concept of zero trust as “never trust, always verify.” Microsoft summarises three guiding principles: verify explicitly, use least privilege access and assume breach: For verification, strong identity proofing and continuous authentication is required. Least privilege restricts the amount of data that a user can obtain. Assuming breach means the design has to take the expectation that there are already attackers within the network, hence segmentation and monitoring are key.
Adoption statistics help to explain why zero-trust is gaining ground. According to a 2025 survey by StrongDM, 81% of organizations have implemented some level of zero trust, and the remaining 19% are planning to do so and no one said zero. A further 84 % are actively pursuing zero trust in order to protect cloud environments and 67 % consider identity and access management and encryption their top priorities. The same survey reports that teams tend to use multiple tools; only 30 percent use unified solutions, which is an indication of the complexity of adoption.
Why traditional approaches fall short
Traditional models of security build walls around a network. Once within the perimeter, the devices and users have wide access. This is not a viable strategy in a world of cloud services, mobile workforces and supply chain partners. Attackers use the element of trust to target legitimate credentials and spread laterally across networks. Zero-trust abandons the concept of “trusted insiders” and secures each of your resources individually. The model is consistent with modern trends such as bring-your-own-device (BYOD), remote working and Software as a Service (SaaS) applications, where users often work outside the corporate boundary.
What is Zero Trust Network Access (ZTNA)?
Zero – Trust Network Access (ZTNA) is a technology that implements the zero – trust principles by brokering secure one – to – one connections between users and the applications they need. CloudFlare describes ZTNA as a method of hiding the IP address of an application, and only accepting connections from verified users, somewhat similar to the way that an unlisted phone number functions. Unlike a virtual private network (VPN) that enables broad network access, ZTNA only allows people to access specific applications and is used to re-verify identity and device posture on a regular basis. Additional data points, such as where the user is requesting them from, the time of the request and what resource is requested, further narrow down access decisions.
Current adoption trends show that ZTNA is gaining ground on legacy VPNs. Tailscale’s 2025 State of Zero Trust report found that 41 % of respondents still rely on legacy VPNs, but 34 % use cloud‑delivered ZTNA and 27 % have adopted peer‑to‑peer mesh VPNs. The study also revealed that fewer than a third of organizations (29 %) use identity‑based access as their primary model; 48 % use a mix of IP‑based and identity‑based approaches and 22 % use IP‑based only. Adoption of just‑in‑time (JIT) access stands at 33 % and only 26 % of organizations said they follow the principle of least privilege. These statistics illustrate that the journey towards fully implementing ZTNA and zero trust is ongoing.

History of Zero Trust Security
The concept of zero trust did not emerge overnight; it evolved through several milestones:
| Year | Event |
| 1987 | A research paper from Digital Equipment Corporation described an early firewall concept, laying foundations for per‑packet trust evaluation. |
| 2001 | IEEE introduced the 802.1X standard, enabling network access control based on client authentication. |
| 2004 | The Jericho Forum promoted de‑perimeterization, advocating for security controls beyond network borders. |
| 2007 | The U.S. Defense Information Systems Agency (DISA) proposed the “black core” model, an early concept similar to zero trust. |
| 2010 | Forrester analyst John Kindervag formally coined the term “zero trust,” challenging implicit trust within corporate networks. |
| 2013 | The Cloud Security Alliance introduced the Software‑Defined Perimeter (SDP), incorporating zero‑trust ideas. |
| 2017 | Gartner proposed the Continuous Adaptive Risk and Trust Assessment (CARTA) model, emphasizing dynamic trust decisions. |
| 2019 | Gartner introduced Secure Access Service Edge (SASE), combining networking and security functions in the cloud. |
| 2020 | NIST published SP 800‑207, which formalized the Zero Trust Architecture (ZTA) and clarified design principles. |
| 2022 | The U.S. Office of Management and Budget issued a memorandum requiring federal agencies to adopt zero‑trust by 2024. |
This timeline shows how zero‑trust matured from research proposals into a mandated framework for government agencies and major enterprises.
Comparison Between Zero Trust and Traditional Security Models
Zero‑trust and traditional perimeter‑based security take fundamentally different approaches:
- Trust assumptions: Traditional models implicitly trust any device or user inside the network. Zero‑trust never trusts any request without verification, even if it originates within the network.
- Access control: Perimeter security grants broad network access once a user has gone through authentication. Zero‑trust grants granular, just‑in‑time access to specific resources based on identity, device posture and context.
- Segmentation: Traditional networks often rely on flat internal networks. Zero‑trust uses segmentation and micro‑perimeters to minimize lateral movement. Each segment is isolated; if an attacker compromises one segment, they cannot easily move to others.
- Monitoring: In a perimeter model, monitoring is often limited to external traffic. Zero‑trust requires continuous monitoring and real‑time analytics across all traffic, including encrypted connections.
- Response to breach: Traditional models assume breaches are rare and focus on preventing them. Zero‑trust assumes breaches will occur; thus designs include mechanisms to detect, limit and contain breaches quickly.
Three Core Principles of Zero Trust
Verify Explicitly
Validate all users and devices before access is granted. This principle requires ongoing authentication and authorization based on many factors – identity, location, device health and usage patterns. Users have to demonstrate identity at every point in a session. Multi-factor authentication (MFA) and single sign-on (SSO) services mean that it is not enough to just have a password, there is some verification process (e.g. biometrics or one-time tokens) that has to be performed. Continuous authentication models monitor throughout the session as opposed to just at login.
Use Least Privilege Access
Limit the permissions of each user to what is necessary to accomplish some task. Users are not granted blanket access to all of the resources but minimum rights for a specific period of time. This strategy which is often called just-enough-access (JEA) and just-in-time (JIT) access minimises the attack surface and minimises the potential damage to be done if credentials are stolen. Tailscale’s survey shows that 56 percent of organizations grant access based on role or need, 33 percent practice JIT access and only 26 percent follow least privilege principles. Such numbers expose the discrepancy between theory and practice and indicate where security teams need improvement.
Assume Breach
Plan as if the attackers already have a foot in the door. Instead of adding defences to stop breaches, in zero trust infrastructures the defences are designed to reduce the blast radius and have the business continuity systems still in place during breaches. By segmenting networks, and validating each and every request, network organizations contain attackers to just a single segment. Continuous monitoring and analytics help detect the malicious activity quickly. This way of thinking promotes the idea of teams that not only invest in prevention but also in detection and response.
Key Implementation Pillars of Zero Trust Architecture
Implementing zero‑trust involves multiple components working together. The pillars below describe key areas.
Identity and Access Management (IAM)
Identity is the new perimeter. DeviceAuthority explains that zero-trust involves ongoing user identity and access privilege verification using multi-factor authentication (MFA) and role-based access control. Single sign on services enhance the user experience without compromising security. Effective IAMs also check for the posture of devices, such as operating system version and security status, before granting access. Organizations should implement policies such as JIT and JEA to grant privileges on a temporary basis and revoke them when they are not required. StrongDM’s report has found that 67 percent of respondents prioritize identity and encryption when implementing zero trust, indicating that IAM is a key pillar.
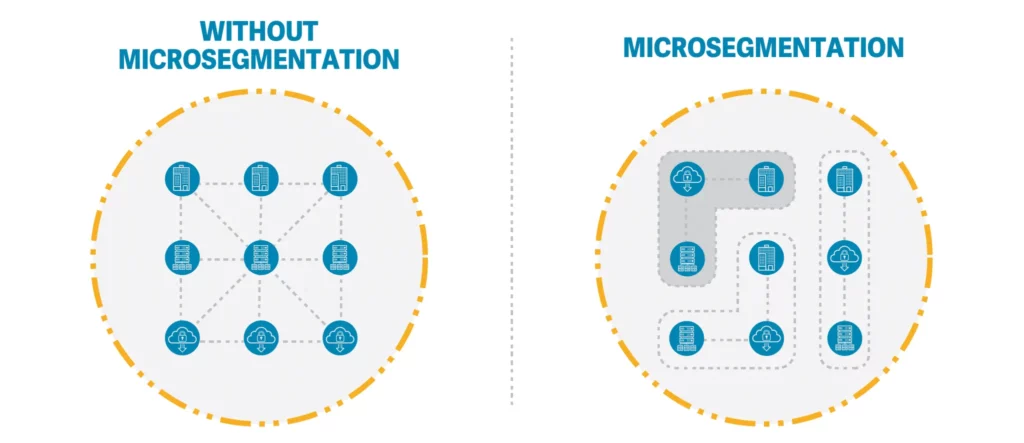
Network Segmentation and Micro‑Perimeters
Segmentation separates crucial resources and prevents the lateral movement of resources. Illumio defines Zero-“Trust Segmentation as Real-time Segmentation of Workloads to Stop Threats from Propagating”. Micro- segmentation means dividing the network into small zones; policies control flow of traffic between the zones based on identity, context and risk. This granular control makes micro-perimeters around applications and data. The approach also enables better visibility, compliance and business resilience.
Endpoint and Application Security
Endpoints – including laptops, mobile devices and servers – are primary entry points for attackers. Netwrix points out that zero trust endpoint security provides continuous verification, least privilege and real-time monitoring at the device level. Organizations should have Endpoint Detection and Response (EDR) tools, Mobile Device Management (MDM) and Mobile Application Management (MAM) solutions to monitor device health and identify anomalies. Just-in-time privilege elevation and privileged access management are effective to help limit administrative privileges. In addition, application security tools also examine user and application behavior to identify unusual patterns. Giám sát hành vi ứng dụng và người dùng bằng User and Entity Behavior Analytics (UEBA) is an important part of this pillar.
Continuous Monitoring and Analytics
Zero trust demands constant visibility of end users and system activity. Continuous monitoring takes data about network traffic, user behavior and device status. Analytics that is powered by artificial intelligence or machine learning identifies anomalies, suspicious patterns and potential insider threats. StrongDM’s research indicates that 60 percent of organizations have real-time monitoring as their top priority in implementing zero trust. Monitor 24/7 và check all the activities of the access and use of AI/ML and detect any abnormalities in real-time to ensure quick detection and response. Centralized dashboards, risk scoring and automated responses enable security teams to respond to security threats before they cause widespread damage.
Benefits of the Zero Trust Model
Reduced cost of data breaches
Zero‑trust strategies measurably reduce the financial impact of security incidents. An analysis of IBM’s Cost of a Data Breach report shows that companies with a fully deployed zero‑trust architecture paid an average of USD 4.15 million per breach, while organizations without zero trust paid USD 5.10 million—a USD 1.76 million difference. SoftActivity notes that this translates to a 43 % reduction in breach costs, with the average cost dropping to USD 3.28 million for fully deployed environments and savings of USD 660,000 even for partially deployed zero‑trust models. Lower breach costs come from limiting attackers’ movement, quickly isolating compromised segments and reducing the scope of data exposure.
Lower cyber insurance losses and improved risk posture
Zero trust helps insurers quantify and reduce risk. A 2025 study by Marsh McLennan’s Cyber Risk Intelligence Center, cited by Zscaler, estimated that deploying a zero‑trust platform could reduce insured cyber losses by 31 % and prevent up to USD 465 billion in annual global economic losses.. The study found that nearly a third of incidents could have been prevented with zero trust if proper cyber hygiene was also in place.. Such findings underline how zero‑trust controls—like continuous verification and micro‑segmentation—limit the blast radius of attacks and reduce the likelihood of paying large insurance claims.
Stronger security for cloud and remote environments
Zero‑trust provides granular access control across hybrid and multi‑cloud environments. It is well suited to remote and distributed workforces because it does not rely on a central gateway; rather, users connect directly to applications through ZTNA after identity and device verification. This reduces latency and improves productivity. Expert Insights notes that cloud deployments of zero trust are growing at 17 % per year. The approach also simplifies compliance across jurisdictions by ensuring that sensitive data remains protected, regardless of where users connect from.
Greater operational efficiency and simplified security architecture
By enforcing standard policies and consolidating control mechanisms, zero‑trust reduces complexity. AuditBoard cites Deloitte research indicating that zero‑trust reduces security costs by minimizing IT complexity through automation and standardization. When identity verification and access enforcement occur through a unified platform, organizations can retire overlapping tools and reduce administrative burden. According to StrongDM’s survey, only 30 % of organizations currently rely on unified solutions. Adopting an integrated zero‑trust framework could improve efficiency and lower operational expenses.
Enhanced compliance and customer trust
Zero‑trust improves visibility and auditability, making it easier to meet regulatory requirements. The SoftActivity report observes that non‑compliance fines average USD 14.82 million, a 45 % increase since 2011. Granular access controls and continuous monitoring support adherence to standards like GDPR, HIPAA and NIST. Demonstrating a commitment to protecting user data can also build customer trust; McKinsey notes that many consumers only buy from companies known for protecting data. By limiting the impact of breaches, zero‑trust preserves reputation and reduces the risk of lawsuits and regulatory penalties.
Common Challenges When Adopting Zero Trust
Despite its benefits, organizations face obstacles when implementing zero‑trust.
Integration complexity and legacy systems
Hybrid environments often include legacy on‑premises systems, private clouds and multiple public cloud services. Tufin points out that integrating these diverse components into a unified zero‑trust architecture can be difficult because of different technology stacks, protocols and security mechanisms. Legacy systems might not support modern protocols or identity‑based controls. Organizations often run multiple cloud service providers with different security tools, so achieving consistent policies requires careful planning. Comprehensive assessments, incremental upgrades, and the use of standard protocols like OAuth and OpenID Connect are recommended for smoother integration.
Resource constraints and skills shortage
Implementing zero‑trust demands financial investment, specialized expertise and additional security tools. Tufin notes that the initial phase can strain resources due to infrastructure changes, increased complexity and the need for continuous monitoring. The 2024 State of Zero Trust & Encryption Study by Ponemon and Entrust found that a lack of in‑house expertise is the top challenge, cited by 47 % of respondents globally and 60 % in the United States. Budget and resource shortages were cited by 46 % of respondents. These figures show that while leadership may support zero trust, investment in personnel and training is still lacking.
Internal resistance and cultural change
Zero trust requires a shift from open networks to tightly controlled access. StrongDM’s survey revealed that 22 % of respondents encountered resistance from internal teams, and 48 % cited cost and resource constraints as challenges. Resistance often arises because users perceive additional authentication steps as inconvenient or fear losing broad access. Overcoming this resistance involves clear communication about the benefits, user training and implementing user‑friendly tools such as SSO and adaptive authentication.
Data visibility and monitoring challenges
Zero‑trust introduces multiple security layers and distributed resources, which complicate monitoring. Tufin explains that gathering and analyzing data across hybrid networks is challenging without advanced monitoring tools, centralized dashboards and user behavior analytics. Organizations must implement real‑time analytics and automation to process large volumes of telemetry and produce actionable insights. Lack of visibility can weaken zero‑trust deployments, so investing in unified dashboards and analytics platforms is critical.

Use Cases of Zero Trust
Zero‑trust principles can be applied across many scenarios. The following examples illustrate how organizations can benefit from the model.
Securing third‑party and contractor access
Enterprises often need to provide network access to contractors, partners and temporary workers. Soliton Systems notes that traditional security models trust devices inside the network, so third‑party access creates significant risk. Zero‑trust treats all users—employees or outsiders—the same: every identity must be verified and granted only the necessary permissions. This approach protects sensitive resources while still enabling collaboration. When “identity is the new firewall,” third parties receive only the access they need, and their sessions are continuously monitored.
Protecting remote workers and cloud resources
Remote work surged after the COVID‑19 pandemic. Traditional perimeter tools such as VPNs or virtual desktop infrastructure are often inefficient and suffer from bandwidth limitations. Soliton’s report explains that ZTNA allows remote users to connect directly to specific applications without routing through the corporate network. This reduces latency and enhances performance. Cloudflare adds that ZTNA periodically re‑verifies user identity and device posture and hides application IP addresses. Remote workers benefit from seamless access while the organization maintains control over who can access what resources.
Supporting globally distributed teams
Distributed teams in satellite offices or on different continents often rely on cloud applications. Traditional security tools can be ineffective because resources are outside the central network. Soliton highlights that zero‑trust enables teams to access resources directly based on verified identity, eliminating the need to backhaul traffic through corporate data centres. This approach improves productivity and reduces latency for global collaboration.
Accessing operational technology (OT) management stations from IT networks
Industrial environments require secure remote access to control systems such as programmable logic controllers (PLCs). Historically, organizations isolated OT networks from IT networks and relied on firewalls. However, this isolation hampers remote maintenance and monitoring. Soliton notes that zero‑trust allows verified users to connect directly to OT management stations, eliminating unnecessary connections and reducing the time spent monitoring these sessions. Safous highlights the urgency: over 54 % of industrial companies suffered ransomware attacks that impacted OT in 2023. A 2023 survey also found that 72 % of OT professionals ranked third‑party access as the leading reason to secure remote access. By integrating multi‑factor authentication, network segmentation and continuous monitoring, zero‑trust enhances OT security and reduces the risk of downtime.
Securing traditional Windows or legacy applications
Some business‑critical applications still rely on outdated protocols or require dedicated clients. Soliton describes cases where these applications depend on Microsoft Active Directory or proprietary communication methods. Zero‑trust can wrap these applications with modern authentication and micro‑segmentation controls, enabling secure access without major redevelopment. This approach provides a bridge between legacy software and modern security requirements.
Enabling supply‑chain and cloud‑to‑cloud connections
Organizations increasingly connect with suppliers and partners through cloud‑to‑cloud integrations and APIs. Expert Insights states that supply chain threats and human risk are key drivers for zero‑trust adoption. By enforcing identity‑based policies and continuous monitoring, organizations can control how third‑party systems interact with their own data. Micro‑segmentation ensures that if one partner is compromised, the attack cannot spread across the network.
Protecting databases and sensitive data
StrongDM’s report shows that 89 % of teams apply or plan to apply zero‑trust to databases, yet only 43 % have robust controls. Databases often store the most valuable assets. Zero‑trust controls—including encryption, tokenization and granular access policies—protect data in transit and at rest. Continuous monitoring detects unusual queries or exfiltration attempts, while micro‑segmentation prevents unauthorized lateral movement.
Conclusion
Zero Trust has evolved into a critical security model for modern enterprises. It replaces outdated perimeter-based defenses with continuous verification, least-privilege access, and an “assume breach” mindset. When implemented correctly, organizations gain stronger protection against ransomware, insider threats, supply-chain risks, remote-access vulnerabilities, and attacks that bypass traditional security layers.
At Designveloper, we understand how essential Zero Trust is for digital-first businesses. Over the years, we’ve helped clients modernize their infrastructures, redesign access flows, and build secure applications that align with Zero Trust Architecture principles. Our experience across web development, custom software engineering, enterprise integration, and cloud-native solutions gives us the technical depth needed to support organizations as they strengthen their security foundations.
We approach every project with a focus on risk reduction, long-term scalability, and security-by-design—whether we’re building a new platform, refactoring an existing system, or consulting on a secure architecture roadmap. Our teams work closely with partners to ensure identity management, access control, endpoint protection, and continuous monitoring align with modern Zero Trust requirements.






Read more topics
You may also like