Remote work has become a permanent – and prominent – fixture in today’s business landscape. While it has presented both organizations and employees with numerous benefits, it has also thrown in new challenges when it comes to cybersecurity. To secure remote access, many made the turn to a certain solution: virtual private networks (VPNs). VPNs play an important role in encrypting traffic and connecting users to internal systems. However, they’re no longer enough to defend against modern cyber threats. Attackers have evolved. That means your security strategies must do the same. This guide highlights why relying solely on VPNs can leave your business vulnerable. It also details additional steps you should consider to effectively bolster your remote work security.
Remote Security: The Role of VPNs
Not long ago, VPNs were seen as a one-size-fits-all solution for remote security. Their function, in summary, is to encrypt tunnels between employees and internal systems. Doing this helps protect sensitive data in transit and enables access to business resources from anywhere in the world.
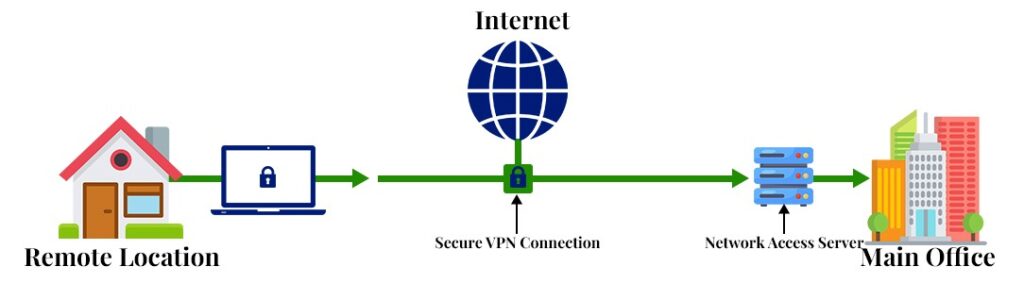
Here’s a more detailed breakdown of why VPNs have been widely adopted:
- Encrypt data traffic: This shields data from potential eavesdropping on public or home networks.
- Internal network access: VPNs extend internal network access to remote users with minimal configuration.
- Cost-effective: It is an affordable, cost-effective solution for businesses to achieve remote connectivity.
- Legacy system support: VPNs support legacy systems that aren’t cloud native.
- Widespread compatibility: Offers broad compatibility with various devices and operating systems.
While useful, it’s important to remember VPNs were built for less complex network environments. As remote workforces grow and cyber threats become more targeted, VPNs no longer supply comprehensive protection on their own.
FURTHER READING: |
1. Invisible Fences: Behavioral Bot Detection That Actually Works |
2. Top 9 Cyber Security Trends to Watch 2026 |
3. What Is Zero Trust? Architecture, Principles, and Use Cases |
VPN Limitations in the Modern Workplace
Make no mistake: VPNs are a solid starting point for remote access. However, in today’s hybrid and remote work environments, they often fall short of modern security demands. Here’s why:
- Overly broad access: VPNs often grant users access to the entire network, rather than simply the resources they require.
- Lack of context-awareness: The lack of context means a VPN doesn’t evaluate a device’s security status, user behavior, or location before granting access.
- Credential vulnerabilities: Without multi-layered verification in place, stolen login credentials can easily be exploited.
- No built-in segmentation: Once inside, users – or even attackers – can potentially move laterally across systems.
- Difficult to scale and manage: VPNs can be resource intensive. They can also be difficult to configure securely across large, diverse teams.
For example, the Colonial Pipeline ransomware attack in 2021 was linked in part to a compromised VPN account that lacked multi-factor authentication. The attackers gained initial access through this weak point – and this led to one of the most disruptive cyber incidents in United States history.
FURTHER READING: |
1. 5 Best Work-Life Balance Tips |
2. Working Remotely Work-Life Balance: What You Should Know? |
3. Remote Executive Assistants: How They Are Changing the Game of Support |
New Requirements for Remote Security
Remote work hasn’t just changed how businesses operate and how attackers exploit vulnerabilities. Unlike traditional office setups, where security could be managed behind a firewall, remote environments are fluid and decentralized. The result: IT teams must defend against dynamic risks. It also means they need more than a VPN.
To put together a layered, adaptable security framework – one built for flexibility and resilience – here are the requirements you need.
Multi-factor authentication
It’s clear that you can no longer rely solely on usernames and passwords in today’s business world. That’s why multi-factor authentication has become essential. It adds an extra layer of security by requiring additional verification, such as a one-time code or fingerprint scan.
It’s a simple step, but this added authentication makes it significantly harder for attackers to breach accounts – even if they’ve stolen login credentials.
Endpoint protection
Remote employees often use various devices of their own. The problem: whether it is a laptop or smartphone, many of these may not meet corporate standards. With endpoint protection tools, you can enforce policies, as well as scan for malware, and track software solutions remain updated.
Cloud-based identity and access management
When SaaS tools and cloud platforms are becoming more prevalent, centralized access control becomes key for businesses. That is where identity and access management (IAM) solutions enter. IAM tools let you define who can access what, and under which conditions. These tools also integrate with single sign-on systems, reducing passport fatigue and improving visibility across user activity.
Zero trust security
Zero trust security, as the name suggests, flips the old “trust but verify” model. It assumes no user or device is trusted by default. With zero trust, access is only granted based on verified identity and other contextual factors. It also supports micro-segmentation, meaning users only gain access to what they need.
Zero trust drastically limits the impact of compromised accounts or insider threats. This makes it a powerful addition to any remote security strategy.
Continuous monitoring
Static security checks at login might have worked in the past, but they are no longer enough. Companies require systems to monitor user activity in real-time. Doing so can flag unusual behavior, such as access to sensitive data during off-hours and logins from unfamiliar locations.
With continuous monitoring, it can trigger alerts and block access when necessary to enhance security efforts.
Patch management
For remote systems, outdated software can provide an easy access point for attacks. Patch management ensures exploits are closed off as soon as possible, keeping everything from operating systems to apps up to date. It’s also wise to utilize vulnerability scanners to identify weaknesses before attackers do.
Automated patching and scanning are essential in a remote work setup to achieve a strong security setup across a distributed workforce.
Conclusion
VPNs were a clever first step when remote work became the norm. However, they no longer offer enough protection on their own. Today’s threats are more targeted and sophisticated, and remote work environments are more complex.
To stay protected, businesses must adopt a modern approach to security. Device compliance, real-time monitoring, zero trust policies – elements like these should be implemented for a more well-rounded defense against cyberattacks.
By evolving your strategy now, it helps safeguard your business in the long term.






Read more topics
You may also like